Concepts¶
Alyvix is a synthetic monitoring system based on computer vision which synthesizes real users without being hardwired to application engines.
NetEye integration with Alyvix allows currently the monitoring of Alyvix nodes, with planned support for scheduling test cases, assigning test cases to sessions on different Alyvix machines, and more.
More information about Alyvix is available on the official website and in the official documentation.
Architecture of Alyvix Nodes¶
This section provides information about the supported Alyvix node types. As explained below, currently NetEye supports four different types of node:
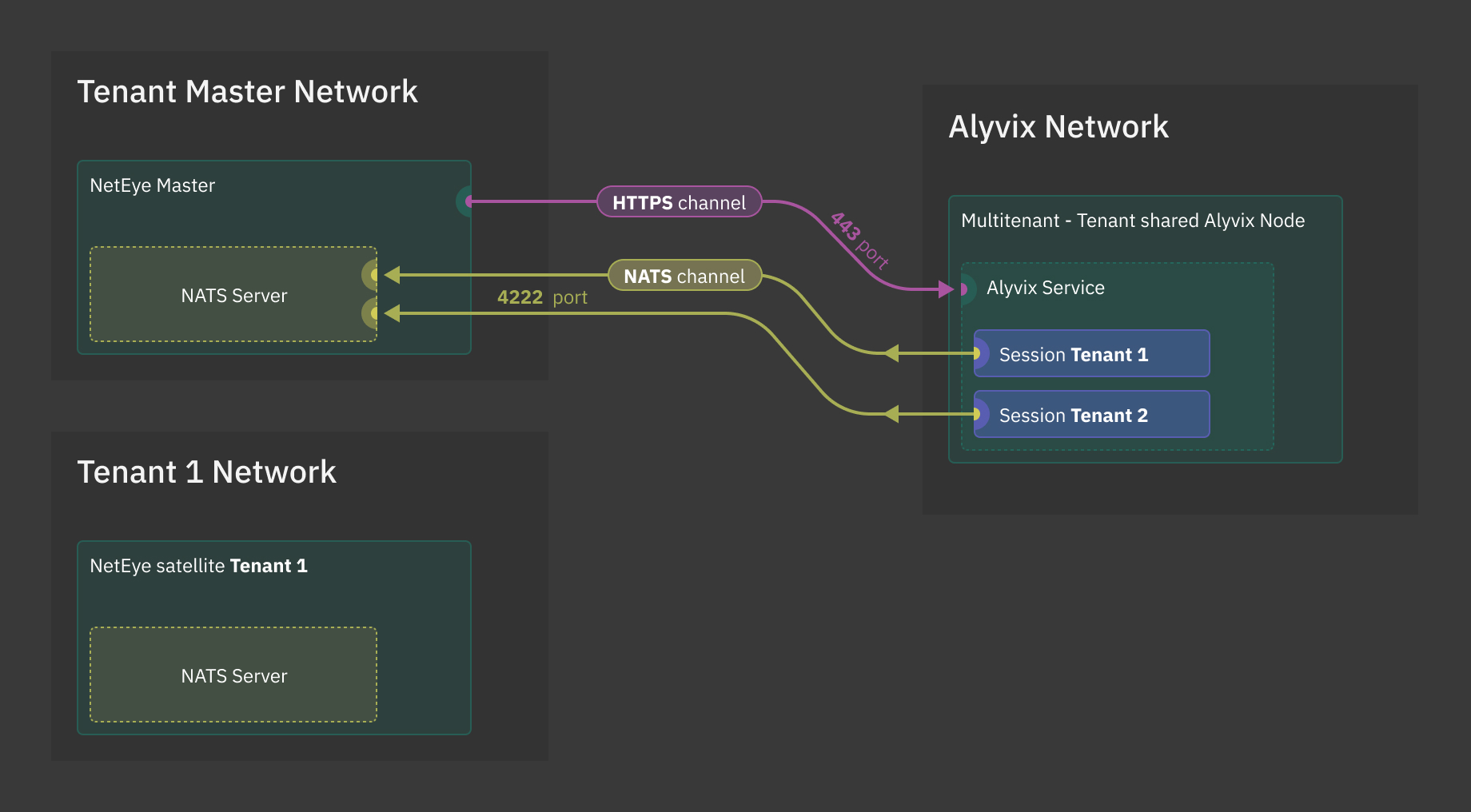
The main differences between them reside in the adopted Tenancy configuration and the way they communicate with the NetEye Master. There are two types of communication involved: HTTPS and NATS. NetEye communicates with the Alyvix Service via API calls through the HTTPS communication channels, while NATS serves as a communication channel to send the performance metrics from the Alyvix nodes to the NetEye Master. The choice of using one rather than the other boils down to your infrastructure and purpose of the node.
Multitenant - Tenant Specific¶
This node is meant to be used in Multitenant environments where the Alyvix node is completely dedicated to and managed by a specific tenant. In this case, the NetEye Master and the Alyvix node can be set up on different networks.
This Alyvix node is dedicated to only one Tenant and hence the communication between the Alyvix node and the NetEye Master will flow through a Satellite of that Tenant. This architecture forces the Alyvix node to run sessions belonging to one specific Tenant, meaning that all the sessions running on a node will be related to one Tenant.
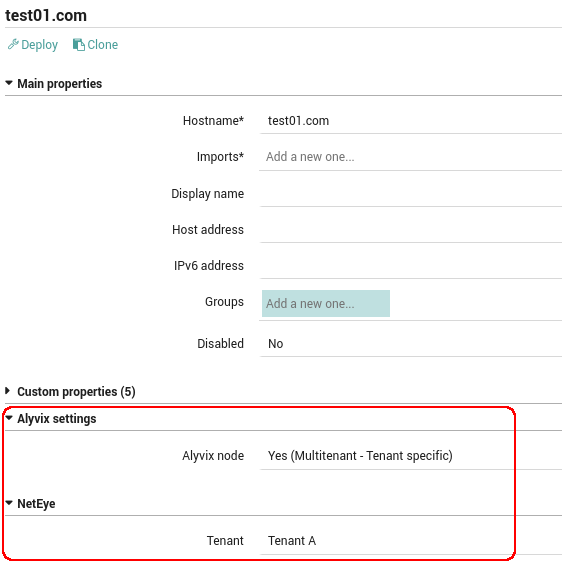
Please note that, to associate a Multitenant - Tenant Specific Alyvix node to a tenant, this must be specified in the Host configuration in the Icinga Director.
Note
This node is currently not fully supported, meaning that the API/HTTP communication is still direct between the NetEye Master and the Alyvix node
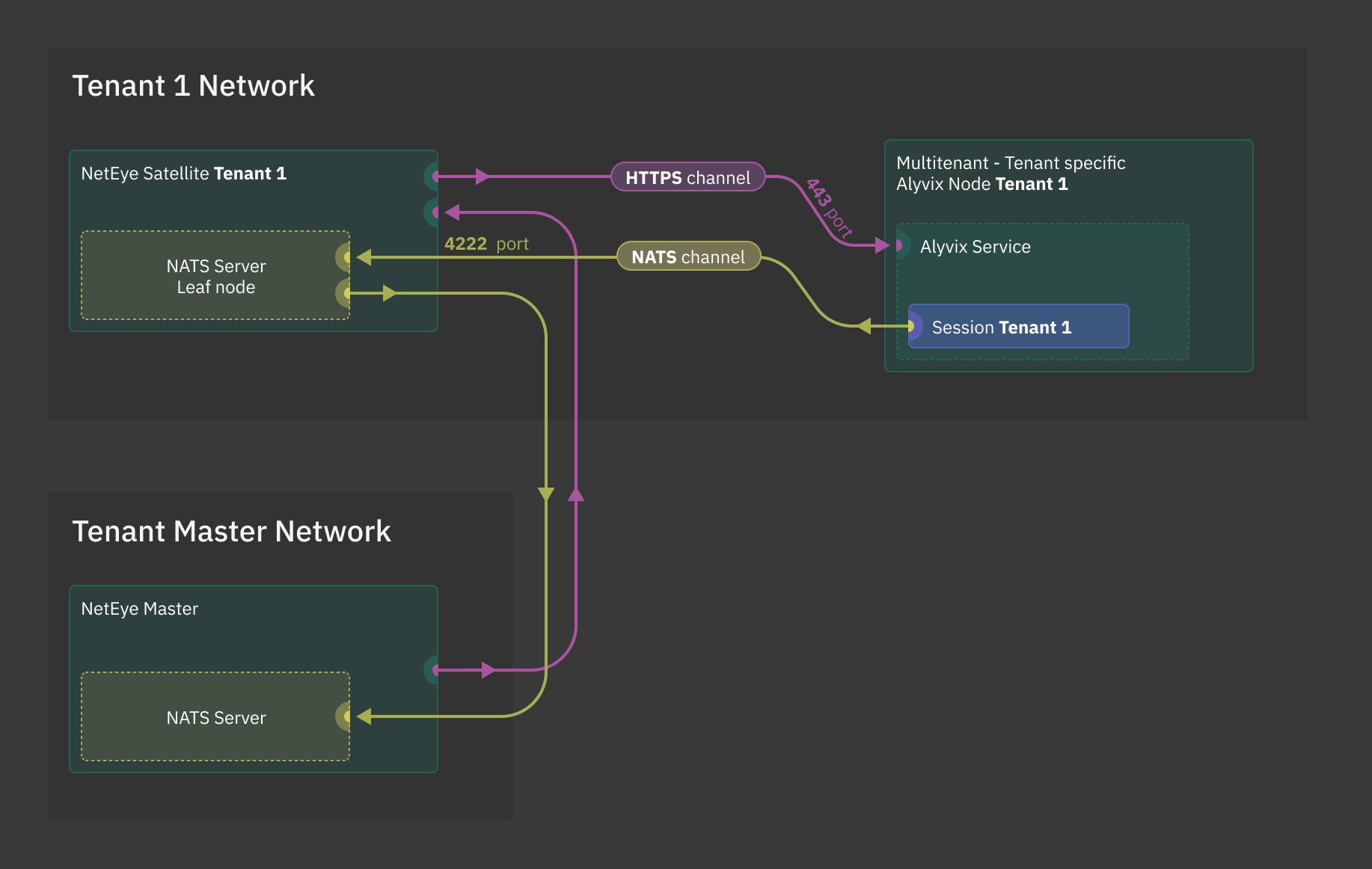
Fig. 230 Communication between the Alyvix node and the NetEye Master through Satellites¶
Single Tenant - Via Satellite¶
This node is equivalent to the Multitenant - Tenant Specific node but for single Tenant environments. Note that in single Tenant environments the only Tenant available is always the Master Tenant.
Note
This node is currently not fully supported, meaning that the API/HTTP communication is still direct between the NetEye Master and the Alyvix nodes
Single Tenant - Direct to Master¶
This node is equivalent to the Multitenant - Tenant Shared node but for single Tenant environments. Note that in single Tenant environments the only Tenant available is always the Master Tenant.
Roles¶
The following roles are currently supported in the NetEye Alyvix integration. For more information about how to configure IcingaWeb2 roles to match the one described below, please consult the User Roles section.
Super Admin¶
A user having the Super Admin role is considered as an administrator of each configured Alyvix node and hence has their full control, with all capabilities.
Tenant Admin¶
A user having the Tenant Admin role is considered as an administrator of one (or more) NetEye Tenants, associated to his role.
As an administrator of a tenant, the user has administrative access on all the Multitenant - Tenant Specific nodes associated with that tenant.
On Multitenant - Tenant Shared nodes, the Tenant Admin has control over objects specific to the tenants under their administration. This includes editing their tenants’ Sessions, creating Test Cases, and monitoring their results. However, they do not have authority to manage global configurations of the node, such as creating new Sessions or managing the license.
Tenant Viewer¶
A user with Tenant Viewer role is granted read-only access to one or more NetEye Tenants associated with their role.
Within the Multitenant - Tenant Specific nodes, the Tenant Viewer can observe all activities and data pertinent to their assigned tenants.
On Multitenant - Tenant Shared nodes, similar to a Tenant Admin user, the Tenant Viewer can view tenant-specific objects, including Sessions and Test Cases, and monitor their outcomes. However, they do not have permissions to observe global characteristics such as configurations, available sessions or licenses.